Intro to VPC
In 2006 when Amazon Web Services (AWS) first launched no one knew how successful its products would be. It was a completely new was to consume & pay for IT resources. Would customers embrace the new paradigm and move their critical infrastructure to a vendor like AWS? Or would they keep with the status quo?
We now know that companies of all shapes and sizes, from the world over, are embracing services like those from AWS. As they adopt such services, the same concerns apply as if they were doing it within their own facilities. Customers want secure, reliable, and cost-effective infrastructure.
At the heart of this is the network. Customers want to be able to apply the same principles of on-premise network design and management to their cloud infrastructure. This includes requirements such as creating DMZ networks, controlling IP address space, and much more.
To meet customer requirements AWS created the Virtual Private Gateway (VPC) service. This service allows customers to design isolated virtual networks withi the larger AWS networking space. Customers can use these networks within the cloud, or as an extension of their on-premise infrastructure.
What is VPC
The Virtual Private Cloud (VPC) allows you to create virtual networks within the AWS cloud environment. These virtual networks are very similar in behavior and design to those that you'd implement in your own datacenter. The main difference being that AWS operates them. Here are some additional characteristics of the service.
Controlled Network Addressing
VPC allows customers to control the private network address spaced used with the AWS cloud. This allows you to design network architectures that are similar to on-premise designs, and that are compatible with your existing network infrastructure.
In addition, when virtual servers (VM) are launched into a VPC, you have the option of using DHCP, or static IP addresses. The VPC can also be used to assign more than one IP address to a given VM.
An Isolated Network in the Cloud
It's important that your network traffic cannot be seen by other AWS customers. The VPC will ensure that you are operating on an isolated network. That means virtual servers you launch in a VPC will only be able to communicate with other instances within your VPC.
Controlled Network Access
The VPC provides excellent access control using Network Access Control Lists (NACLs). These operate like on-premise network device NACLs. You can created numbered lists of rules that that either allow or deny traffic. These NACLs are stateless, meaning that responses to permitted inbound traffic are subject to the rules for outbound traffic.
An Extension of Your Network
AWS designed VPC to be an extension of your network. That means you can establish a VPN connection to the VPC, and communicate with the network as if it were just another datacenter. Because you control the VPC private network address space, and all NACLs, you can ensure that virtual servers within AWS are accessible to the right on-premise networks.
The Default VPC
Each new AWS account is created with something called a Default VPC. The Default VPC allows you to begin using AWS EC2 (virtual servers) right away, without any additional configuration required.
In this lesson we will explore the Default VPC in order to understand some of the most basic VPC concepts.
The Default VPC Diagram
The following diagram shows all of the components involved in the Default VPC. This is not all of the components that can be involved in a VPC. But it is a good place to start when learning about the service.
Take a moment to study the diagram. Below the diagram is an introduction to each component.
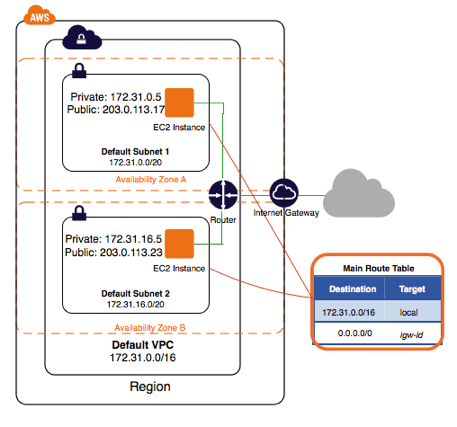
Source: AWS VPC Documentation
Let's review this diagram now, from the outter resources inward.
Region
VPCs are created in a specific region. Regions are a group of two or more Availability Zones. If you've yet to learn about the AWS Regions, you can take a look at this map to see where their regions reside.
VPC Network Space
The Default VPC comes with a pre-assigned network address space of 172.31.0.0\/16. The subnets created within the Default VPC will be based off this network space.
Availability Zone
VPCs span Availability Zones (AZ) within a given Region. In this diagram you see that there are two zones being used in this network design; A & B.
Subnets
The main network space is split into subnets. Subnets define a portion of the overall network space, and are confined to one AZ. The Default VPC are public subnets, meaning that any instances within the subnet can access the internet.
Instance
The diagram shows two EC2 Instances; one in each subnet. These instances have two IP addresses. One address is private, and is assigned via DHCP from the subnet address space. The second is a public IP address assigned by AWS from their pool of public facing IP addresses.
Route Table
A key concept to VPC in general (not just the Default VPC), is that of a route table. This route table controls the routing for the entire subnet. This table can do things like route traffic to the internet (default behavior), or to another network device.
Internet Gateway
The last resource to cover is the Internet Gateway. The AWS documentation says:
An Internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the Internet. It therefore imposes no availability risks or bandwidth constraints on your network traffic. An Internet gateway serves two purposes: to provide a target in your VPC route tables for Internet-routable traffic, and to perform network address translation (NAT) for instances that have been assigned public IP addresses.
The Default VPC is configured to route traffic from its subnets to the Internet Gateway device.